Configuration of Authentication and Authorization
Valid for versions from 20.03 and up
Explanation
Authentication and Autherization in the PEPJ system is now configured via a JSON file that is written to the database through a migration tool.
Two authentication options:
-
Local Active Directory
-
OpenID Connect
Config file
When using Local Active Directory, there is no need to modify any Json file.
When using OpenID, its configuration file "Configuration/OpenIdConnectConfiguration.json" needs to be modified to obtain access through the PEPJ system
Example of this file:
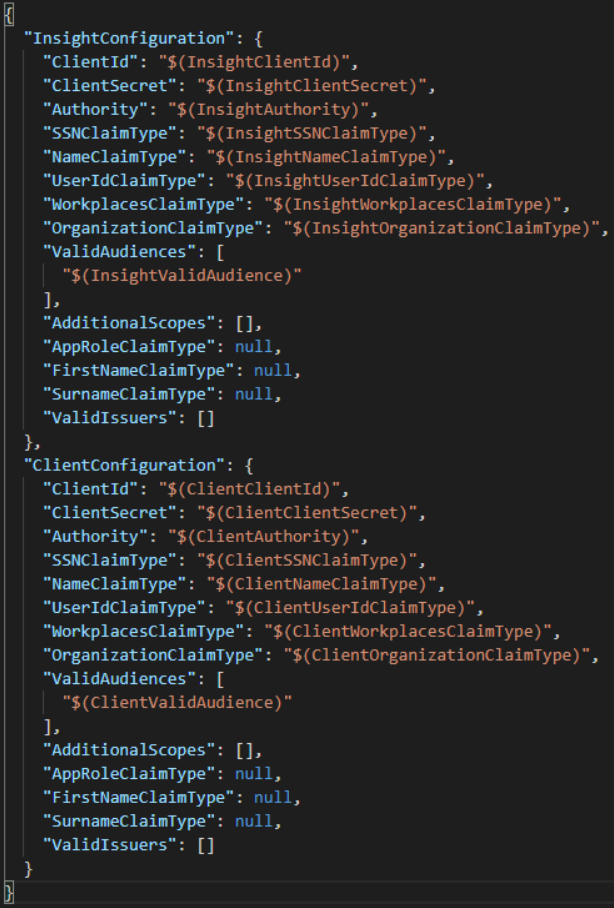
Text editor: Visual Studio
The example file shows configurations of OpenID Connect for Insight and Client
Client settings are used by ClientHub to authenticate and validate access tokens sent from the client.
Changes done in this file need to be saved to the database via the migration tool
| Field | Use |
|---|---|
| ClientId: | Is given through the authentications provider used. |
| ClientSecret: | Is given through the authentications provider used. |
| Authority: | The authentication endpoint used |
| SSNClaimType: | Sets path to the SSN in the token |
| NameClaimType: | Sets path to the username in the token |
| UserIdClaimType: | Sets path to the user id in the token |
| WorkplacesClaimType: | Sets path to the workplace in the token |
| OrganizationClaimType: | Sets path to the organization in the token |
| ValidAudiences: | A list of ValidAudiences that can be authenticated |
| AdditionalScopes: | A list of extra scopes the services requests. Standard scopes are "openid" and "profile". |
| AppRoleClaimType | Sets the path to the roles in the token. If null, the system will attempt to use standardized claim types as roles |
| FirstNameClaimType og SurnameClaimType | Can be set if the token contains names split over several claims. If these values are empty, the system will only look for a full name in the claim type defined by "NameClaimType" |
| ValidIssuers | May contain a list of approved authentication providers. If this value is empty, the system wil use providers from the "well-known" section defined by "Authority" |
Configuration of Client
When using OpenConnect authentication, a "settings.json" needs to be modified with authentication configurations.
Example of such a modification:
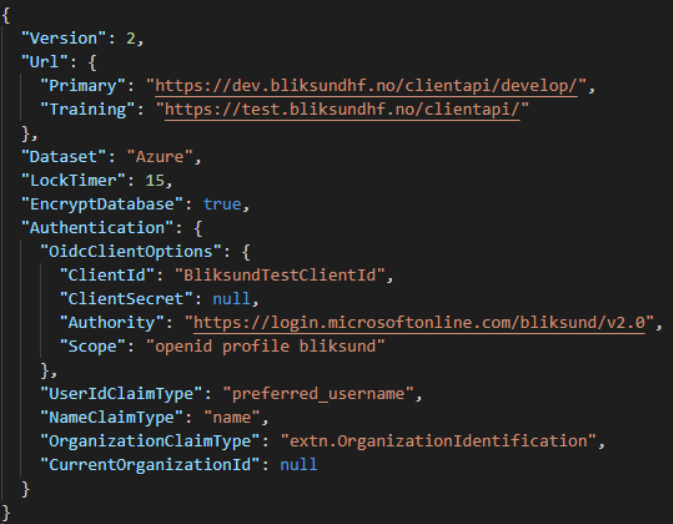
Text editor: Visual Studio
| Field | Use |
|---|---|
| OidcClientOptions | Contains the general settings the client needs for the user to log on. |
| "ClientId" | Contains client id used with the authentication provider. |
| "ClientSecret" | A "secret" value used by some authentication providers. Some providers demand it be null. |
| "Authority" | The authentication endpoint used. |
| "Scope" | Contains what scopes the client shall request from the provider. A minimum scope for OpenIdConnect would be "openid profile". |
| UserIdClaimType | Contains path to user ids in the token |
| NameClaimType | Contains path to name of the user in the token. |
| OrganizationClaimType | Contains path to the organization in the token. |
| CurrentOrganizationId | May contain a value dictating wether only logins by users from the specified organization will be accepted by the client. If empty, all successful logins will be accepted. |
Graphical method - Local Active Directory
To graphically configure and save using the migration tool, follow these steps
First, run the migration tool
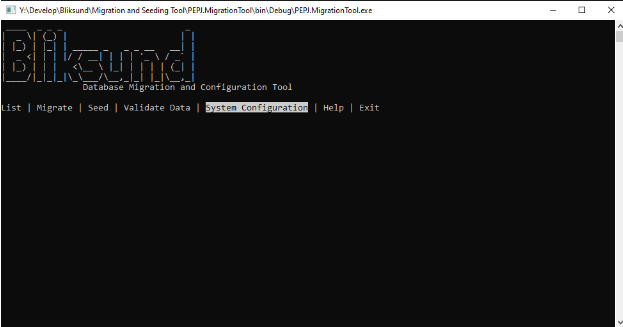
Select "System Configuration"
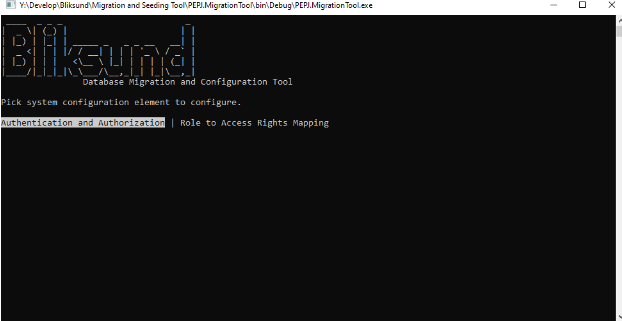
Select "Authentication and Authorization"
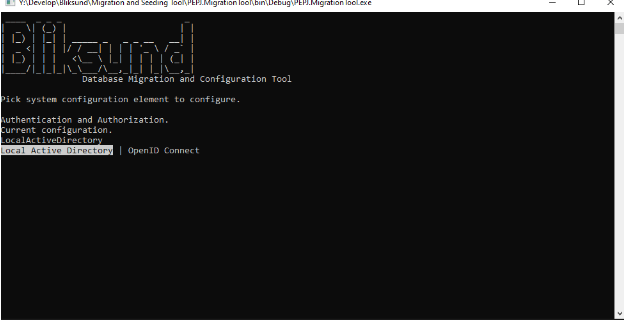
Select "Local Active Directory"
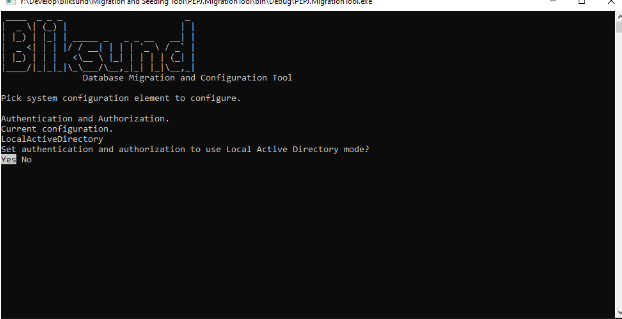
Select "Yes"
When done, the following message will display.
![]()
Graphical method - OpenID Connect
To graphically configure and save using the migration tool, follow these steps
First, run the migration tool

Select "System Configuration"

Select "Authentication and Authorization"
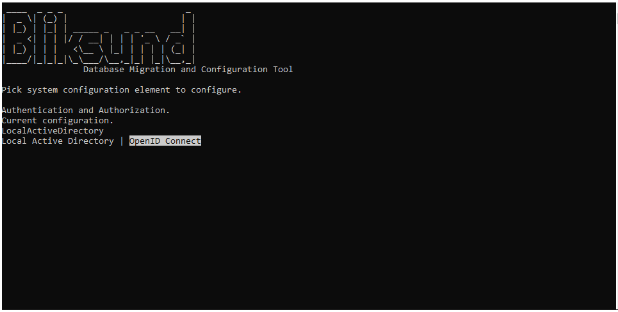
Select "OpenID Connect"
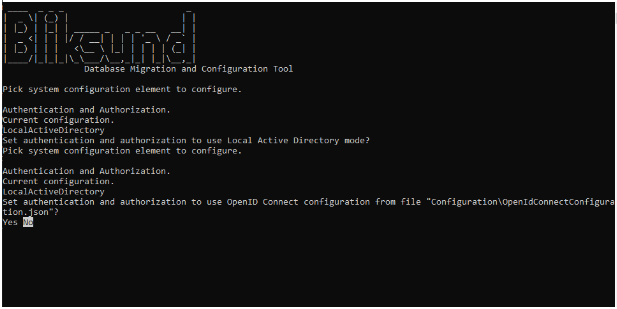
You will then be informed that it sets the configurations based on the "Configuration/OpenIdConnectConfiguration.json" file.
Select "Yes"
When done, the following message will display.
![]()